The evidence bank: leveraging security's most valuable asset
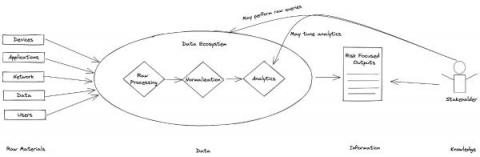
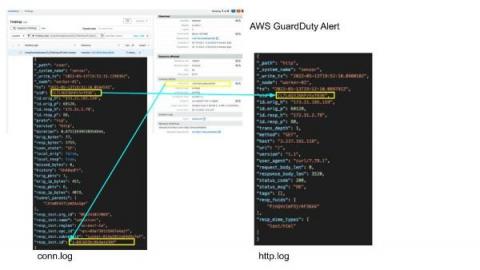
Evidence is the currency cyber defenders use to pay down security debt, balancing the value equation between adversaries and the enterprise. Defenders can use evidence proactively, identifying and protecting structural risks within our zone of control. Evidence can also be used reactively by supporting detection (re)engineering, response, and recovery activities, guiding us back to identifying and protecting structural risks.