Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
November 2021
Hands-On Muhstik Botnet: crypto-mining attacks targeting Kubernetes
Malware is continuously mutating, targeting new services and platforms. The Sysdig Security Research team has identified the famous Muhstik Botnet with new behavior, attacking a Kubernetes Pod with the plan to control the Pod and mine cryptocurrency. A WordPress Kubernetes Pod was compromised by the Muhstik worm and added to the botnet. On the Pod has been deployed and executed various types of crypto miners, like xmra64andxmrig64.
Getting started with runtime security and Falco
Discover how to get started with Falco to overcome the challenges of implementing runtime security for cloud-native workloads. If you are adopting containers and cloud, you are probably enjoying benefits like automated deployments and easier scalability. However, you may also find that when it comes to security, this is a whole new world with new rules, and traditional security tools struggle to keep up. As a new paradigm, cloud-native environments need new cloud-native tools.
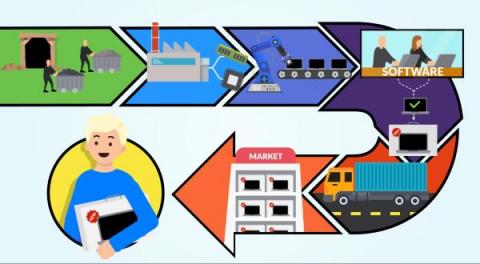
Secure software supply chain: why every link matters
The new threats in software development are not only related to the specific company itself. The whole software supply chain is a target for attackers and it is really important to make sure that we put all our effort into securing each link because if one fails, everything will be affected. Supply chain activities include each step of the transformation of raw materials, components, and resources into a completed product, and its delivery to the end customer.
Malware analysis: Hands-On Shellbot malware
Malware analysis is a fundamental factor in the improvement of the incident detection and resolution systems of any company. The Sysdig Security Research team is going to cover how this Shellbot malware works and how to detect it. Shellbot malware is still widespread. We recorded numerous incidents despite this being a relatively old and known attack that is also available on open Github repositories.