"Chain"ging the Game - how runtime makes your supply chain even more secure
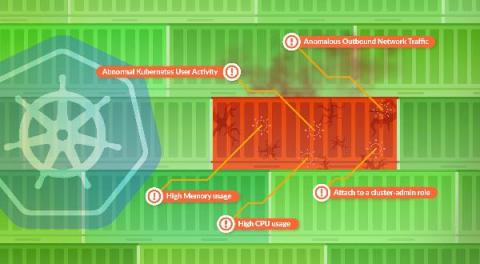
There is a lot of information out there (and growing) on software supply chain security. This info covers the basics around source and build, but does it cover all of your full software supply chain lifecycle? Is your build env at runtime protected? Is your application post deploy protected at runtime? This article will not only discuss what these concepts are, but provide additional discussions around the following: Read on brave reader…