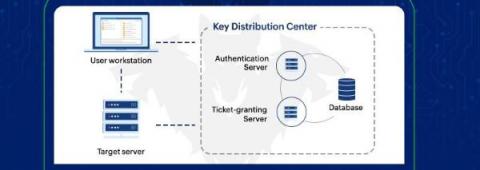
Five worthy reads: Privacy vs. monetization
Since the advent of the internet, personal data has been collected by internet companies in exchange for free services or content. This barter was also intended to provide personalized services to users. However, these data harvesters started selling data to advertising agencies for huge profits, which resulted in predatory marketing efforts towards internet users.