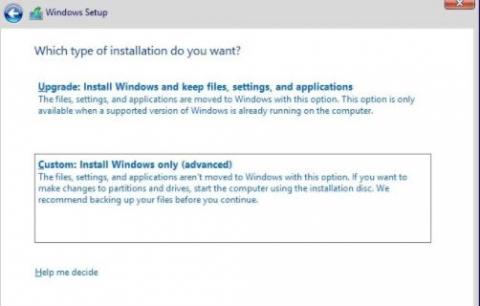
Five worthy reads: Are we ready for a passwordless future?
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we explore the possibilities and challenges of a passwordless era.