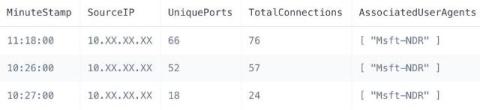
Why DORA Makes MTTR the Board's Business
Based on our reading, the Digital Operational Resilience Act (DORA), is at a fundamental level, a transformative ICT challenge. DORA makes the speed and accuracy of security threat detection and response a board-level concern. Fail to stop, classify and report on cyber incidents accurately and, from 2025 onwards, your organisation could face a fine of 1% of global turnover.