Door-To-Door Scams: Common Types and How They Work
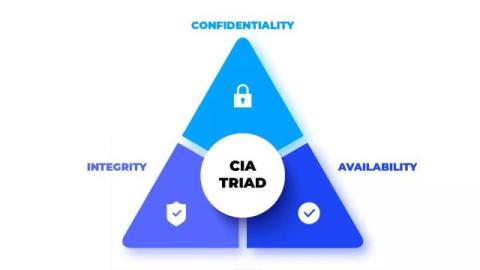
Over the years, door-to-door scams have become rampant, targeting unsuspicious homeowners with various tactics. The door-to-door scam involves individuals disguising themselves as sales representatives or service providers to access people's homes to gain personally identifiable information like social security numbers, properties, or money. There are various door-to-door scams, and understanding how they work is crucial to protecting oneself and the community.