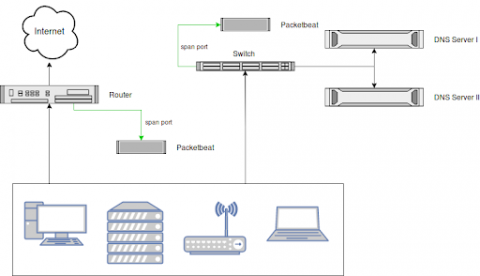
Security Log Monitoring and DNS Request Analysis
Monitoring all DNS requests in your network, including those that were blocked by (e.g., by a firewall) is a great way to increase visibility, enforce compliance and detect threats. A common problem with collecting DNS logs is that DNS server logs are notoriously hard to parse. Also, parsing only the logs of your DNS servers leaves a blind spot when it comes to usage of, or the attempt to use, an external DNS server like Google's 8.8.8.8.