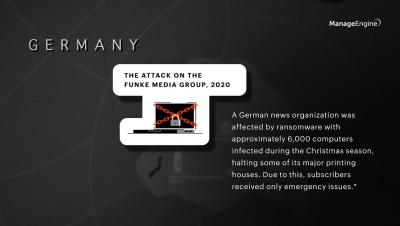
7 features key to a unified and proactive endpoint security solution
This year’s Cybersecurity Awareness Month has come to an end and, with every passing year, cyberthreats are increasing in number and complexity. Reactive solutions are no longer enough to confront cyberattacks. Organizations must implement proactive strategies to secure their IT assets.