The Concerning Lack of Transparency in Bug Bounty Programs
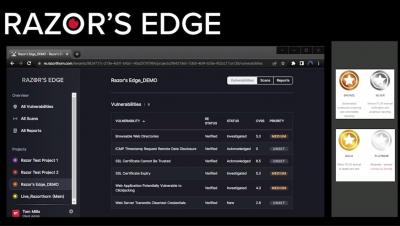
In this video, James Rees shares his concerns about the lack of transparency in bug bounty programs. He highlights the fact that testers are not always properly vetted or regularly checked, leaving companies unsure of who is testing their systems. He also notes that certain regions tend to have more malicious actors, raising questions about the validity of testers from those areas. This lack of transparency can be concerning for companies and users alike, and James encourages more accountability and validation measures to be put in place for bug bounty programs.