Combining External Attack Surface Management and Crowdsourced Security Testing - Webinar Recap
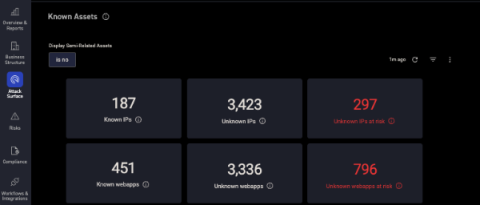
Bugcrowd offers crowdsourced security testing through a community of white hat hackers. CyCognito offers automated discovery of an organization’s externally exposed attack surface. Combined, the two solutions allow for a comprehensive inventory of exposed assets to be included in the scope of bug bounties or pentests.