Redacting Message Fields for Privacy Purposes
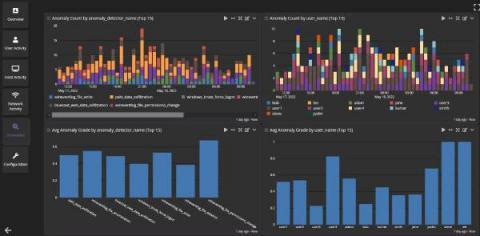
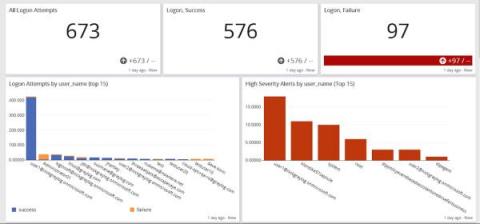
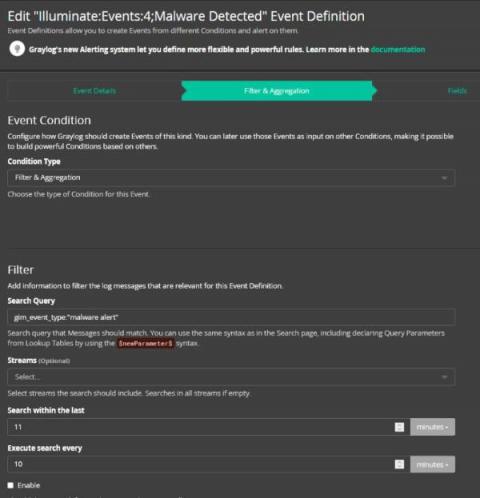
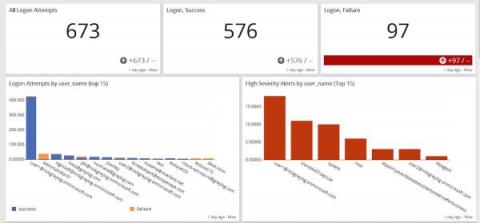
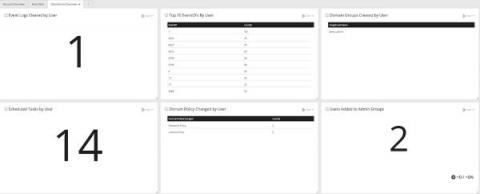
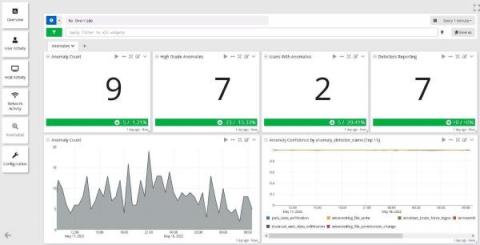
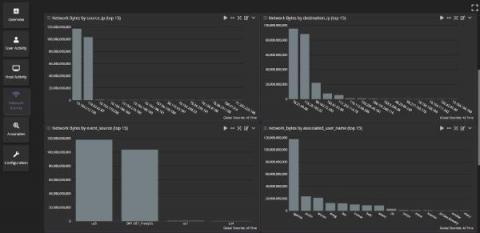
Many organizations today have strict data privacy regulations that they must comply with. These privacy regulations can often clash with the requirements of security, application and operations teams who need detailed log information. At Graylog, many of the organizations who use our tool are logging sensitive data that may contain personally identifiable information, health related data or financial data.