Dissecting The Cobalt Strike Beacon
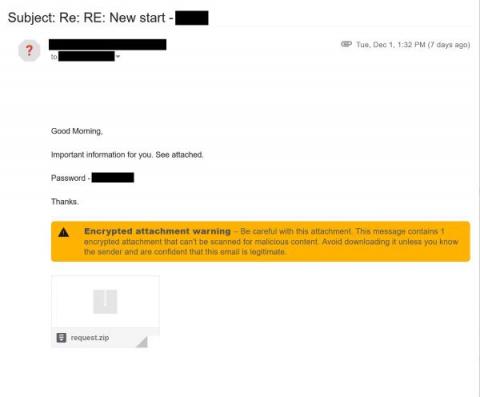
In a previous article, we introduced a piece of malware that ThreatSpike detected in December 2020, moving laterally between hosts. The attack consisted of two components: A text editor repurposed as a launcher for the actual payload, identified as Cobalt Strike’s Beacon.