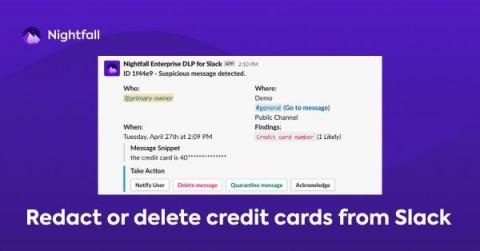
The 4 Step Guide to Adding DLP to Communication Services
With this short guide we will explain how you can add data loss prevention (DLP) as code to communications services like Twilio and SendGrid in a few lines of code, helping ensure your customer communications remain compliant.