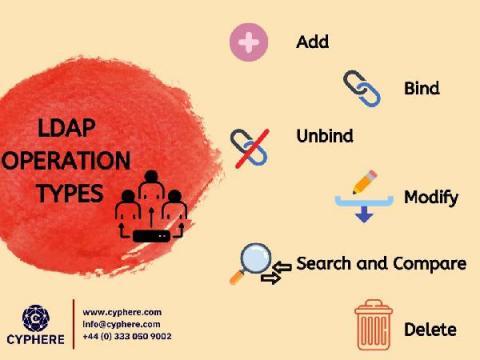
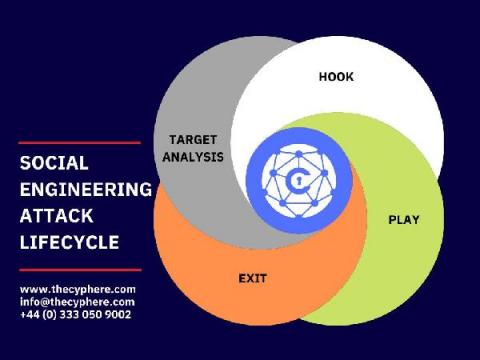
What is LDAP Server? How does it work?
The Lightweight Directory Access Protocol (LDAP) is a cross-platform vendor-neutral software protocol used for directory service authentication. For simplicity, imagine the LDAP server as a comprehensive virtual phone book. The phone book gives access to an extensive directory of contact information for hundreds of people. Using LDAP, it is easy to search through the phone book and find whatever information is needed.