Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DataTrails
15 Ways to Make SBOM Distribution Easy
The whole point of an SBOM is lost if you keep it a secret. Here we reveal our secrets of the ideal SBOM exchange. Let us know if we’ve missed anything in RKVST SBOM Hub. SBOMs are made for sharing and are the gifts that keep on giving, but only if they get to the right place at the right time to drive the right critical decision. The first critical decision, or moment of truth, is whether to buy a vendor’s product.
SBOMs are the gifts that keep on giving.
The timing of CISA’s SBOM-a-rama today and tomorrow coincides with the fallout from the “vulnerability of the decade” gifting the industry with yet another example of why scaling and operationalizing the widespread use of SBOMs is so vital. Log4Shell is a 10/10 vulnerability in a hugely popular Java logging library – Log4j – used in virtually every online service. For two decades it was considered harmless, that is until last week when somebody found it wasn’t.
SBOM Sharing Should be Easy. Now it is!
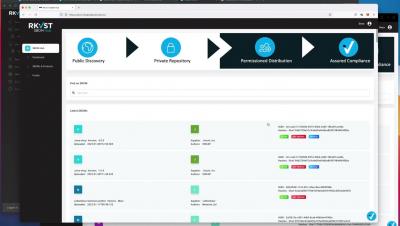
Today we’re pleased to announce the RKVST SBOM Hub – the first place to find and fetch SBOMs. RKVST SBOM Hub is a secure, immutable, any-to-any framework that integrates into both publisher and subscriber workflows to massively simplify the effective sharing of SBOMs to help all parties comply with the Executive Order. Try it out for yourself here.
Sharing Is At The Heart Of SBOM Value
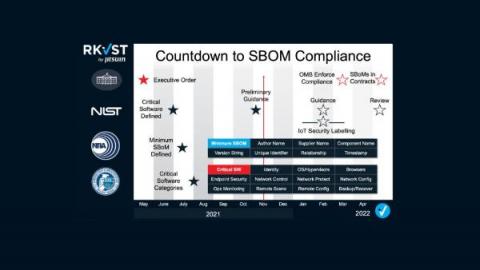
The Presidential Executive Order made it clear that the status quo, where the hidden vulnerabilities in cyber supply chains left doors wide open to attackers, can no longer be allowed to persist. It correctly identified transparency as the key principle to build trust and Software Bills of Material as a critical first step of the solution. But while much of the current debate is focused on how to build SBOMs, further and deeper thinking is needed on how to share them.
RKVST SBOM Assurance
RKVST - About
Why RKVST?
Do you want to archive old emails now? We’ve all seen the prompt and many of us choose to consign thousands of emails to an uncertain fate, protected (somewhere) in case we should ever need to cover our arses in some future argument. But this paints a very limited and negative picture of the importance and indeed relevance of archives. Today archives are associated with rearward-facing research, often seeking to uncover a truth long after alternative facts have taken hold.