New Kroll report highlights rise in use of external remote services for initial access
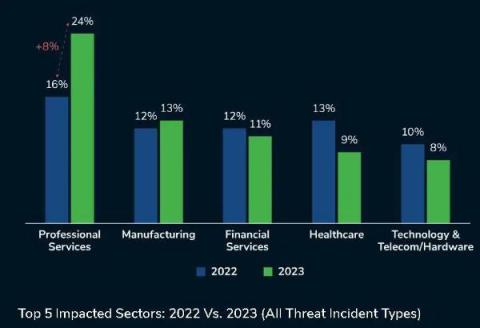
Q4 2023 presented a complex security landscape with a mix of both positive and negative trends On the one hand, activity associated with larger ransomware-as-a-service (RaaS) operations, such as LOCKBIT and BLACKCAT, declined due to the success of major takedown operations. However, negative patterns also continued, like the ongoing focus of threat actors on the professional services industry.