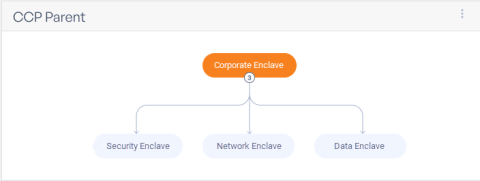
Save Time and Steps with Ignyte's Control Inheritance Automation
If you are managing multiple GRC frameworks for multiple environments, then you know how powerful it is to have clearly-defined and repeatable work processes to enable teams to work together efficiently. To enable efficiency within the organization, Ignyte has launched common control provider capabilities within the platform for 100+ customers.