Cyber Threat Intelligence Series: A Lens on the Healthcare Sector
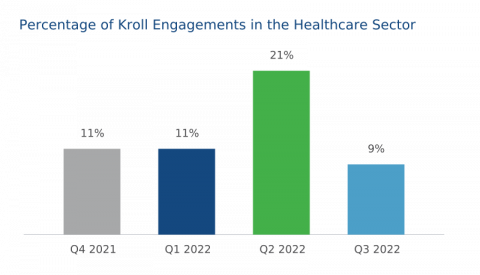
A review of recent Kroll incident response cases consistently proves that the healthcare industry is one of the most frequently targeted sectors. This observation mirrors what is experienced by national cybersecurity agencies as multiple warnings have been launched during 2022, highlighting how ransomware gangs and nation state actors are now aggressively targeting healthcare institutions.