Aligning Falco's Cloudtrail Rules with MITRE ATT&CK
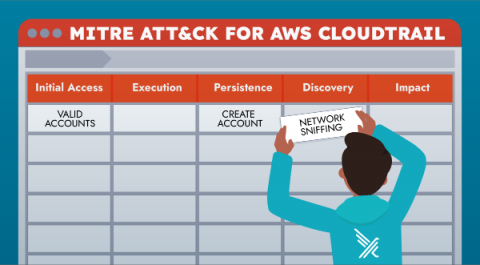
This blog will explain how Falco’s Cloudtrail plugin rules can be aligned with MITRE ATT&CK Framework for Cloud. One important note is that the team at MITRE has developed several different matrices to address the unique risk associated with adversaries in the cloud, in containerized workloads as well as on mobile devices.