How the Russia-Ukraine conflict changed cyber attacks: More attacks, More DDoS
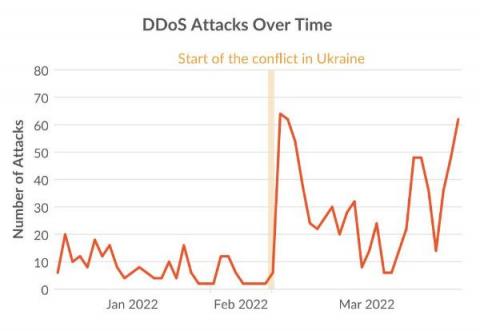
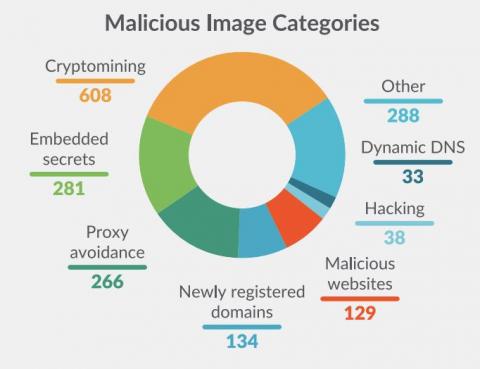
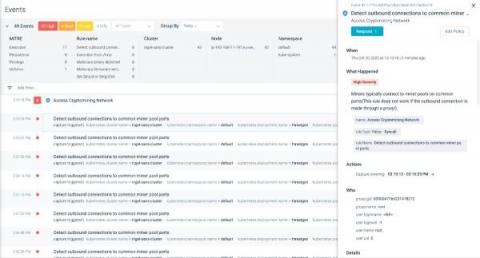
The conflict between Russia and Ukraine includes a cyberwarfare component with government-supported threat actors and civilian hacktivists taking sides. The goals of disrupting IT infrastructure and utilities have led to a 4-fold increase in DDoS attacks between 4Q21 and 1Q22. Over 150,000 volunteers have joined anti-Russian DDoS campaigns using container images from Docker Hub.