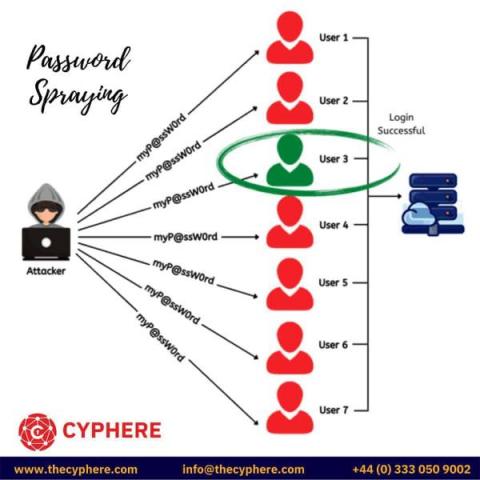
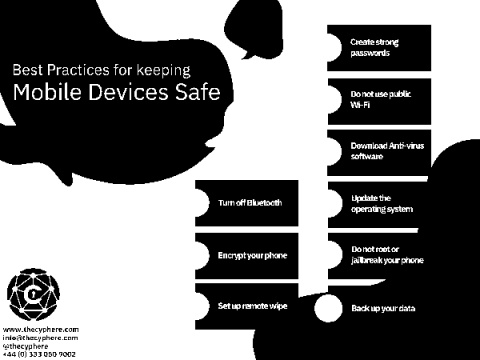
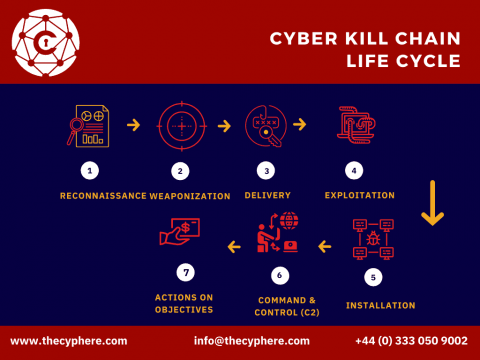
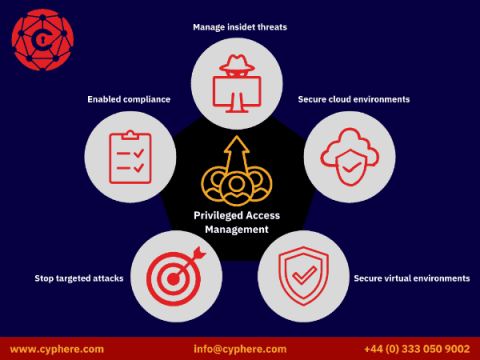
What is a Brute Force Attack? Tools, Examples & Prevention steps
Passwords are an easy way to implement an authentication mechanism in which the user is asked to enter a string of characters (that he had chosen) to log in to his accounts. We will cover brute force attacks, types and examples in this blog article.