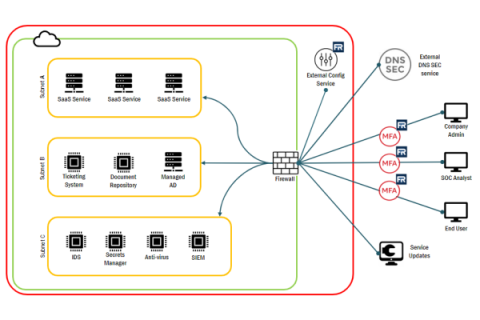
Understanding FedRAMP System Boundaries
In the ever-changing world of technology, staying secure is a top priority for many organizations. Identifying and documenting system boundaries is essential for keeping data safe and secure, but what does this mean? In this article, we’ll explore system boundaries, how to identify them, and how to generate system boundary diagrams. By the end of this guide, you’ll be well-versed in understanding system boundaries and creating diagrams that can help keep your information secure!