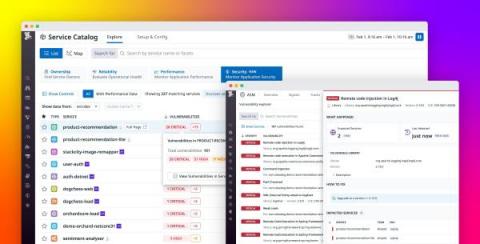
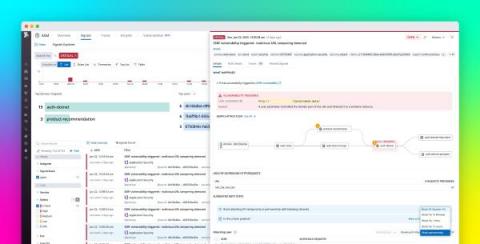
Best practices for detecting and evaluating emerging vulnerabilities
Identifying and evaluating security vulnerabilities is essential at every stage of software development and system management. New vulnerabilities surface all the time, demanding ongoing vigilance as well as effective methods of assessment and response. And recent data shows that this is increasingly the case.