Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
January 2023
This Month in Datadog: Cloud Security Controls Ruleset, New Test Coverage Page, and more
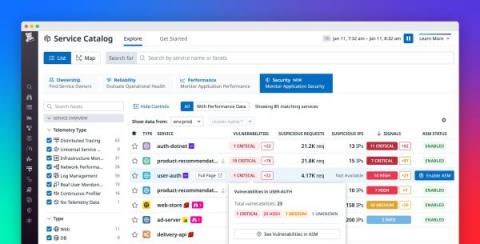
Gain visibility into risks, vulnerabilities, and attacks with APM Security View
As your business grows and your services scale in number and complexity, it’s difficult to maintain a rapid pace of innovation while keeping your applications secure. It’s particularly challenging to respond to attacks, as DevOps and security teams need to collaborate to understand each attack’s root cause and remediate the vulnerabilities that enabled it.
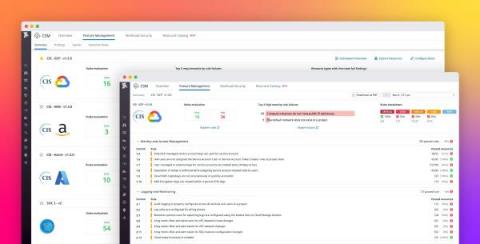
Improve the compliance and security posture of your Google Cloud environment with Datadog
Organizations are scaling their environments at a rapid pace, deploying thousands of cloud resources, services, and accounts. Because of their size and complexity, these environments are more susceptible to compliance issues—a misconfiguration in a single cloud resource can lead to costly data breaches. For that reason, organizations are prioritizing governance, risk, and compliance (GRC) management to ensure that their environments are configured appropriately.