|
By Komodo Research
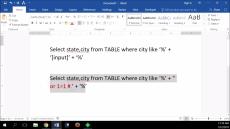
A lightweight, PowerShell-based SMB enumeration and data-gathering tool for red team engagements and penetration testing. This tool is designed to work natively on Windows without the need for external dependencies like Python or Linux-based utilities.
|
By Komodo Research
Server Message Block (SMB) is a ubiquitous protocol used for file sharing, remote access, and resource management across enterprise networks. While critical for business operations, its misconfigurations can expose vulnerabilities to attackers. In this blog post, we’ll dive into a real-world red team operation where a simple yet effective PowerShell-based tool led us from SMB enumeration to full network takeover.
|
By Komodo Research
Server Message Block (SMB) is a ubiquitous protocol used for file sharing, remote access, and resource management across enterprise networks. While critical for business operations, its misconfigurations can expose vulnerabilities to attackers. In this blog post, we’ll dive into a real-world red team operation where a simple yet effective PowerShell-based tool led us from SMB enumeration to full network takeover.
|
By Komodo Research
Managing sensitive data while meeting compliance and security standards is an ever-growing challenge for organizations. Today, secure data management is a top priority, especially in industries like healthcare, finance, and fintech. This focus is expected to intensify in the coming years. To address these needs, privacy vault solutions like Databunker, Skyflow, and Piiano have emerged. Each offers unique capabilities tailored to specific use cases.
|
By Komodo Research
Cybersecurity is a critical and complex challenge for every business in today’s digital world. However, not every business has the resources, expertise, or time to manage its security effectively and efficiently. That’s where CISO as a Service comes in. CISO as a Service is a flexible and scalable solution that provides you with access to a dedicated and experienced Chief Information Security Officer (CISO) and their team of security professionals.
|
By Komodo Research
Last week I met with a Director of a European Bank. A question he asked me was "How much should we spend on Cyber Security"? As there is no one-size-fits-all answer to this question, I will try to break it down: Small Businesses (1-50 employees): Secure Your Startup/ SMB/ SME Medium Businesses (51-500 employees): Step Up Your Game Large Businesses (500+ employees): Go Big on Security Enterprise Level (5000+ employees): Fortify the Fortress Bonus Tips Practical Steps Invest in Cybersecurity.
|
By Komodo Research
PDF Exports: Hidden SSRF Risk In the realm of cybersecurity, understanding vulnerabilities is paramount to safeguarding sensitive data and maintaining the integrity of systems. One such vulnerability that often lurks in the shadows is SSRF, or Server Side Request Forgery. While SSRF vulnerabilities have been extensively discussed in various contexts, today, we're going to delve into a unique perspective – exploring SSRF vulnerabilities through the lens of HTML to PDF exports.
|
By Komodo Research
Our healthcare client faced a security threat through PDF generation on their platform. We discovered a flaw that allowed harmful code to be included in PDFs, enabling us to access internal server files and services as well as obtaining AWS credentials. Taking proactive steps is vital to protect healthcare systems from such vulnerabilities.
|
By Komodo Research
As the cybersecurity landscape continues to evolve, the importance of rigorous and proactive security measures has never been more pronounced. The Network and Information Security (NIS2) Directive, an initiative by the European Union, is set to redefine cybersecurity standards for essential and important entities, emphasizing the need for robust risk management, incident response, and business continuity planning.
|
By Komodo Research
Imagine a world where digital fortresses are impervious to cyber threats – a utopia for any cybersecurity professional. Yet, we live in a realm where one misstep in cloud configurations opens the gates to potential havoc. As someone who has journeyed through the labyrinth of cybersecurity for over two decades, I've witnessed firsthand how a simple misconfiguration can escalate from a minor hiccup to a full-blown security nightmare.
|
By Komodo Consulting
A short clip to demonstrate how a vulnerability in Firefox detected by Komodo's research team can lead to a file-less adware.
|
By Komodo Consulting
Step by step instruction by Komodo's expert on how to solve the first challenge.
|
By Komodo Consulting
Don from ITProTV Interviews Boaz Shunami, Komodo Consulting's CEO at RSA 2017. Boaz explains how Komodo's team delivers unique value to its fortune 500 customers with external Red-Team vs. Blue-Team exercises.
|
By Komodo Consulting
CYSNIFF is a preemptive Cyber Threat Intelligence Platform designed to help organizations and governments deal with the rapid increase of cyber threats such as planned Cyber Attacks, DDoS attacks, Persistent Threats and data Leakages. By providing real-time alerts generated automatically by our unique Artificial Intelligence engine, your organization receives prompt notifications regarding major cyber events of interest and can respond proactively.
- February 2025 (1)
- January 2025 (2)
- November 2024 (1)
- August 2024 (1)
- June 2024 (1)
- April 2024 (2)
- February 2024 (1)
- January 2024 (1)
- October 2023 (2)
- August 2023 (3)
- July 2023 (2)
- June 2023 (1)
- May 2018 (1)
- August 2017 (1)
- March 2017 (1)
- May 2015 (1)
Komodo Consulting enables companies to align their business and regulatory requirements and adapt to the ever-changing challenges of the information and cyber security fields.
Utilizing proprietary tools and techniques and an expert approach we provide our customers with a full range of cyber security services ranging from Application Security, Incident Response, Threat Intelligence, Training, and Penetration Testing through to Cyber Security Strategy, Risk Assessments and more.
Our Services:
- Black Box Penetration Testing: Full-spectrum, black and white box penetration testing of your systems, networks and applications to find vulnerabilities an attacker could exploit.
- Red-Team Security Testing: Our red-team engagements test resilience to real-world cyber-attacks targeting Fortune 500 companies based on the TIBER-EU framework.
- SOC2 Penetration Testing: Our Black Box Penetration Testing services uncovers hidden vulnerabilities and help achieve SOC 2, PCI, HIPAA, and ISO 27001 compliance.
- Cloud Security Assessment: We offer expert cloud security assessments for AWS, GCP, and Azure, ensuring businesses safeguard their digital assets.
- Application Security: Our team of AppSec experts has you covered for all your needs – from security assessments and design reviews to application security training.
- Third-Party Risk Management: We provide third-party risk management services for businesses, assessing security, supply chain continuity, and compliance to mitigate potential risks.
With thousands of successful Penetration Testing and Red-Team Security Testing for more than 100 happy clients, you're in the right hands.