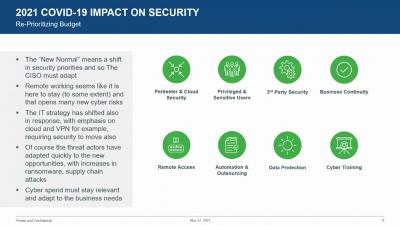
Setting the cyberscene: Leading with a security first mindset
Our current global landscape is testing resiliency. As organizations continue to shift to a remote work business model, the rush to digitally transform has created new and heightened cyber risk concerns. Protecting these digital connections needs to stay top of mind for leaders looking to help their organizations adapt to these changes while continuing to innovate. In this blog, we will look to set the cyberscene and focus on a security first mindset.