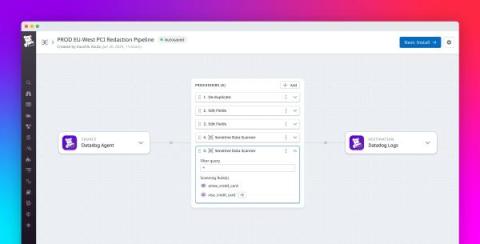
Redact sensitive data from your logs on-prem by using Observability Pipelines
As your business evolves to serve more users, your applications and infrastructure will generate an increasing volume of logs, which may contain sensitive data such as credit card numbers, IP addresses, and tokens. When you collect sensitive data, you may be subject to laws such as GDPR—which restricts the transfer of personal data across borders, and you may face legal consequences if this data is exposed outside your infrastructure.