|
By Outpost 24
Philadelphia, PA, 22nd April – Outpost24, a leading provider of cyber threat exposure management solutions, is pleased to announce the addition of manual asset rescans to its External Attack Surface Management (EASM) platform. This enhancement enables EASM customers to re-check the status of recently updated assets, providing flexibility around asset management tasks outside of automated and continuous scanning.
|
By Marcus White
Ever lost sleep over possible hidden attack routes lurking in your organization’s attack surface? You’re not alone. The concept of ‘unknown-unknowns’ is a recurring nightmare for many IT professionals – but there are ways to mitigate the risks. We’ll explore the problem of unknown-unknowns and provide some practical strategies to help your organization uncover these hidden threats.
|
By KrakenLabs
Welcome to the Threat Context Monthly blog series where we provide a comprehensive roundup of the most relevant cybersecurity news, and threat information from KrakenLabs, Outpost24’s cyber threat intelligence team.
|
By Marcus White
A penetration test is a sanctioned assault on your organization’s electronic assets and data. If the attack is repelled, you win. If the attack successfully breaches your defenses, technically you also win – as you’ve now got the chance to fix those vulnerabilities before a real attacker tries their luck. Given the complexity of a modern enterprise, a pen test can evaluate a wide range of assets, networks, systems, and apps on premises, mobile, and in the cloud.
|
By KrakenLabs
Welcome to the Threat Context Monthly blog series where we provide a comprehensive roundup of the most relevant cybersecurity news, and threat information from KrakenLabs, Outpost24’s cyber threat intelligence team.
|
By Marcus White
Finding savings and efficiencies is part of an IT leader’s role. But sacrificing security for the sake of convenience is almost always asking for trouble later down the line. There are IT security shortcuts that might be well-intentioned and seem sensible at the time, that could have serious and unintended negative consequences. We’ll run through nine common IT security shortcuts that can end up costing organizations millions.
|
By Peter Kantomaa
During a recent customer assessment, our pen testers discovered a critical vulnerability that exemplifies the importance of manual and continuous pen testing. The issue involved a feature intended for administrators, allowing them to send messages to a “broadcast” endpoint, which would then be displayed in a modal pop-up box for all logged-in users of the web application. However, our pen testers found that this functionality was accessible to any user, regardless of their role.
|
By Victor Acin
A recent advisory issued by the Cybersecurity and Infrastructure Security Agency (CISA) has shed light on vulnerabilities in Ivanti VPNs that are currently being actively exploited by malicious actors. Ivanti VPN solutions, widely utilized for their robust security features and efficient network management capabilities, have recently been identified as containing critical vulnerabilities.
|
By Agon Hysenaj
Cross-Site Scripting (XSS) attacks pose a significant security threat by infiltrating an application’s input fields with malicious code snippets. When users access the affected pages, this code is executed in their browsers, putting their sensitive information at risk. The malicious content injected into the web browser can take various forms, including JavaScript, HTML, Flash, or any other executable code.
|
By KrakenLabs
Welcome to the Threat Context Monthly blog series where we provide a comprehensive roundup of the most relevant cybersecurity news, and threat information from KrakenLabs, Outpost24’s cyber threat intelligence team.
|
By Outpost 24
There’s a gap between the identification of vulnerabilities and the IT resource available to remediate them within the timeframe hackers operate. With Outscan NX and Farsight, the vulnerability risk management process becomes more streamlined and efficient, enabling organizations to proactively address the biggest risk first to optimize security resource.
|
By Outpost 24
Penetration testing is an effective way to detect flaws in your application before they turn into a serious threat, helping you better understand the applications attack surface. But in the always-on economy there comes a problem - traditional pen testing delivery takes weeks to set up and the results are point in time, which leaves critical application vulnerabilities exposed longer than it should - given the average time for a threat actor to weaponize a new vulnerability is only 7 days.
|
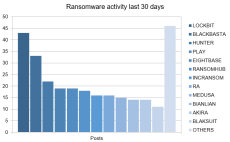
By Outpost 24
Ransomware has continued to grow in maturity throughout the first half of 2021. As businesses struggle to understand yet another major attack that hit the Kaseya supply chain, organizations are beginning to realize data backups and cyber insurance alone won’t save them.
|
By Outpost 24
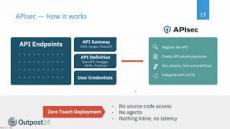
APIs are a key part of modern web applications and a growing security challenge that isn’t well understood by developers and application security managers, leading to exposed APIs that give hackers access to sensitive data. Find out how to secure your APIs and prevent vulnerabilities from making it into production.
|
By Outpost 24
The sheer volume of vulnerabilities security professionals have to deal with everyday poses a significant challenge to resource and time to patch. Learn how to narrow down high risk CVEs by focusing on exploit availability and threat context beyond CVSS.
|
By Outpost 24
Demands for cybersecurity are growing. Are you providing the solutions customers seek and need to improve their security competence and prevent data breach? Find out how to differentiate from local competitors by partnering with Outpost24.
|
By Outpost 24
Added links in Outpost24 Scale DAST tool to Secure Code Warrior for findings with a CWE. Where an Appsec finding is linked to a CWE we have introduced direct links to Secure Code Warrior eLearning training platform. This gives users the ability to understand what the vulnerability is and more importantly how to address these findings within their development process. Customers do not have to be customers of Secure Code Warrior (SCW) to enjoy the learning modules presented, though customers who are SCW customers may get further insights as well as tracking scores and other metrics.
|
By Outpost 24
We don’t think it’s fair that businesses are targets of cybercriminals. That's why we’ve created the most complete security assessment platform to help our customers tighten their 'full stack' security exposure before their business can be disrupted.
|
By Outpost 24
As zero trust moves higher up on the CISOs security agenda we’re hosting a webinar to discuss the pros and cons of adopting this new approach and how it can impact your team’s ability to remain agile, whilst protecting your business. As a recent study demonstrates, 34% of security breaches involved insiders in 2019 meaning CISOs are becoming more likely to consider zero trust and it should come as no surprise that many organizations are now eager to adopt a zero-trust security policy.
|
By Outpost 24
Join Outpost24 and 360 Trust Services experts to learn how you can tackle the growing cybersecurity threats, and secure your high availability operations and satisfied customers. Save your spot for a comprehensive webinar, as we will be presenting the latest security products and services offerings, based on 20 years’ experience and accumulated expertise in cybersecurity, from vulnerability management, risk prioritization to driving a remediation culture.
|
By Outpost 24
Web app attacks remain the #1 vector exploited in successful breaches. With agile development, apps run the risk of creating new vulnerabilities or perpetuating old ones on a weekly, daily, even hourly basis, security and risk managers need to step up a programmatic response. Fortunately there's a new, collaborative model for Appsec that organizations can operate in a mostly automated manner. Download our useful DevOps guide and learn how best to operationalize security testing in an agile process.
|
By Outpost 24
More and more companies choose to migrate to a Cloud infrastructure to take advantage of new resources, an elastic storage power and agile deployment, nevertheless IT professionals are not always trained to secure these new technologies. Like traditional infrastructures, a public Cloud infrastructure services requires the implementation of security measures and controls by their users. Enterprises must adapt their security policy to these new technologies to reap the Cloud benefits without increasing their cyberattacks exposure area.
|
By Outpost 24
We surveyed over 200 security professionals at the 2020 RSA conference to delve deeper into the dangers of rogue access points and understand how security professionals are tackling wireless security. Our data highlights their main concerns and the key trends from IT and network security professionals on the wireless security frontline. Key findings in the 2020 Internet of Evil Things report: Download the 2020 IoET Report to uncover valuable wireless security insights to help protect your organization's network airspace in the future.
|
By Outpost 24
Cloud is the new fact of life for providing enterprise IT services. However, security professionals are left feeling unclear about the complexities surrounding cloud, shared responsibility and understanding where the cloud provider security tools from AWS, Azure and Google Cloud Platform are falling short.
|
By Outpost 24
Are you struggling to triage through tons of findings to identify the greatest threats and patch more effectively? You are not alone! With speed being the biggest challenge to effectively patch, this whitepaper looks at how existing prioritization works with CVSS scoring and how a risk based approach with machine learning can be applied to align corporate risk appetite and drive better decision making for optimal efficiency.
- April 2024 (4)
- March 2024 (4)
- February 2024 (3)
- January 2024 (6)
- December 2023 (2)
- November 2023 (4)
- October 2023 (5)
- September 2023 (3)
- August 2023 (3)
- July 2023 (7)
- June 2023 (4)
- May 2023 (2)
- April 2023 (4)
- March 2023 (3)
- February 2023 (3)
- January 2023 (2)
- December 2022 (2)
- November 2022 (2)
- October 2022 (4)
- September 2022 (2)
- August 2022 (2)
- July 2022 (5)
- June 2022 (2)
- May 2022 (5)
- April 2022 (1)
- March 2022 (5)
- February 2022 (4)
- January 2022 (1)
- December 2021 (2)
- November 2021 (2)
- October 2021 (1)
- September 2021 (1)
- August 2021 (3)
- July 2021 (2)
- June 2021 (3)
- May 2021 (4)
- April 2021 (2)
- March 2021 (3)
- February 2021 (8)
- January 2021 (1)
- December 2020 (6)
- November 2020 (9)
- October 2020 (8)
- September 2020 (7)
- August 2020 (2)
- July 2020 (5)
- June 2020 (4)
- May 2020 (9)
Effortlessly automate identification of web application, network infrastructure, wireless and cloud vulnerabilities with a risk based approach for fast remediation.
Over 2,000 customers worldwide trust Outpost24 to assess their devices, networks, applications, cloud and container environments and report compliance status. We serve leading organizations across a wide range of segments including financial services, government, healthcare, retail, telecommunications, technology, and manufacturing.
Full stack security scanning and penetration testing:
- Single Platform, Total Coverage: Servers, endpoints, devices, switches, apps, clouds and containers. We got you covered in a single UI with risk based insights.
- Developed by Ethical Hackers: It takes a hacker to stop a hacker. We built years of ethical hacking experience into our products and services for best vulnerabitity results.
- Continuous Security Testing: Our tools work around the clock to automate scans and orchestrate security controls to protect you on a continual basis.
Complete vulnerability and security assessment.