Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
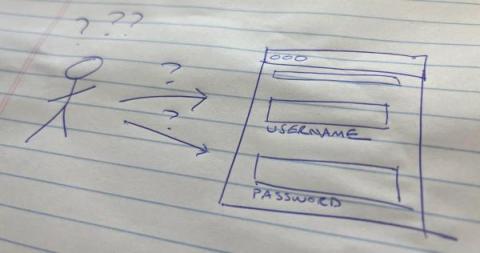
My Username Fields Have Passwords in Them! What Do I Do?
SOAR'ing to Success: How a Leading Software Vendor Monitors FTP Traffic
Software vendors have loads of high-value data they need to protect — from customers’ personally identifiable information to the company’s intellectual property — so a data breach can be catastrophic. There’s a lot on the line if these types of organizations fall victim to a cyberattack, including fines from regulators or damage to their brand and reputation.
Year in review: ManageEngine Log360's analyst recognition from 2022
Cyberattacks have intensified over the last few years as threat actors are always improvising their game plan to carry out new and sophisticated methods. Concepts like Ransomware as a Service have made it easy for small threat groups to leverage weaponized services with devastating results for organizations. This highlights how traditional security systems and approaches are no longer able to keep up with the ever-evolving threat landscape.
SOAR'ing to Success: How a Major US Bank Streamlined their SOC
According to the 2022 IBM Cost of a Data Breach Report, the global average cost of a data breach is $4.35 million. Data breaches in the US are even more costly, averaging over $9 million. However, it isn’t just the big players caught in the line of fire. IBM’s report also found that 83% of companies will experience a data breach soon, meaning financial institutions of all sizes — from local credit unions to Fortune 500s — are at risk.
SOAR'ing to Success: How an Insurance Company Automates Threat Hunting
Many automation tools, such as SOAR, suffer from an ironic Catch-22: you know that automation will save your team huge amounts of time, but it’s difficult to implement and requires skills you don’t necessarily have in-house. Essentially, you can’t afford the tools that will save you money. Ay, there’s the rub! You may have seen tools promising “no-code” capabilities with intuitive GUIs that help non-programmers build abstract functions.
Sysdig Secure-Google Chronicle Integration - Why, What and How
Cloud adoption and digital transformation have enlarged attack surfaces that can be exploited by malicious actors to harm your organization. Traditional SIEMs and EDRs fall short as they are not cloud-native and also difficult to scale. Further, there are inherent fixed costs that need to be considered when adopting any modern threat detection apparatus.
Explore the Splunk SOAR Adoption Maturity Model
This past June I presented a.conf22 session called “A Beginner’s Guide to SOAR: Automating the Basics” to address perceptions about SOAR adoption among security practitioners. This was my first in-person presentation to a live audience in several years because of the pandemic and I was encouraged to find that the session was among the highest attended at the event with well over 200 attendees in the room.
How Automation Playbooks Double Down on the Value of SOARs
So you’ve set up a Security Orchestration, Automation and Response (SOAR) platform. You’re now ready to detect, respond to and remediate whichever threats cyberspace throws at you, right? Well, not necessarily. In order to deliver their maximum value, SOAR tools should be combined with playbooks, which can be used to drive SOAR systems and ensure that SOARs remediate threats as quickly as possible — in some cases, without even waiting on humans to respond.
Introducing Tines Labs
Tines empowers anyone to automate their manual work, regardless of complexity, without writing a single line of code. Many teams starting on their SOAR journey often don't know what processes can be automated and find it challenging to translate their manual work into software-based solutions. In cybersecurity, automating repetitive processes at scale is a relatively new idea with little public research to support it.