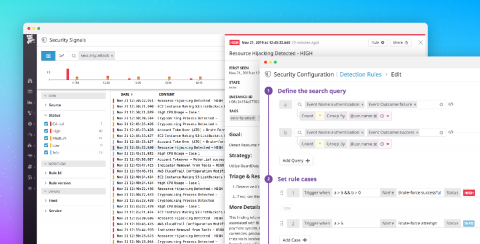
Announcing Datadog Security Monitoring
With the growing complexity and velocity of security threats in dynamic, cloud-native environments, it’s more important than ever for security teams to have the same visibility into their infrastructure, network, and applications that developers and operations do. Conversely, as developers and operations become responsible for securing their services, they need their monitoring platform to help surface possible threats.