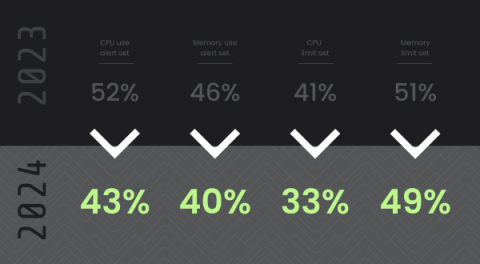
5 reasons why observability and security work well together
Site reliability engineers (SREs) and security analysts — despite having very different roles — share a lot of the same goals. They both employ proactive monitoring and incident response strategies to identify and address potential issues before they become service impacting. They also both prioritize organizational stability and resilience, aiming to minimize downtime and disruptions.