Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
How to Leverage DevOps and Automation to Bolster Security
Speed and security. Old-fashioned thinking contended that the two were incompatible; that high-velocity development and deployment of apps and software services invariably introduced higher levels of risk. However, it has become increasingly apparent that speed is a necessary aspect of security. The stakes are sky-high, with some estimates projecting that the annual cost of cybercrime losses and damage will reach $6 trillion by 2021.
Investigate and Correct CVEs with the K8s API
When NIST (https://nvd.nist.go) announces a new CVE (Common Vulnerability and Exposure) that impacts Kubernetes, kube administrators and IT Security teams need to quickly understand the impact of the vulnerability and protect their Kubernetes clusters. Often, no patches are yet available, so in addition to understanding the impact, DevOps teams have to decide whether or not to create a custom fix to mitigate the risk of that CVE without bringing down the entire app or system.
How to implement guardrails for AWS EKS
Today marked the first ever AWS re:Inforce security conference, and Styra was well represented. Paavan Mistry from AWS took the stage to walk through an EKS Security session with Synamedia, wherein they talked about the great responsibility organizations have over their Kubernetes environments.
Gravity v6 UI Tour
12 Common Tools for Your DevOps Team
DevOps is revolutionizing the way enterprises deliver apps to the market by blending software development and information technology operations. This convergence creates an assembly line for the cloud, as Tim Erlin wrote for The State of Security, by increasing the rate at which companies can develop apps and deliver them to users.
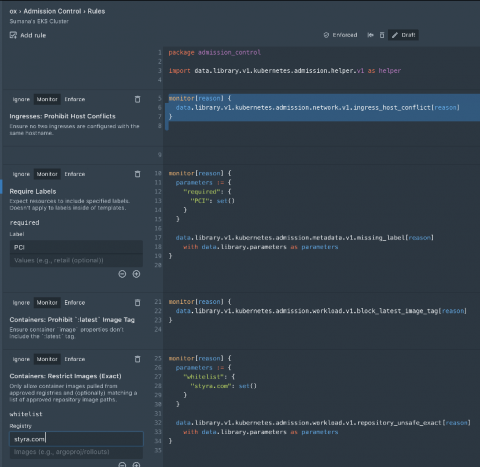
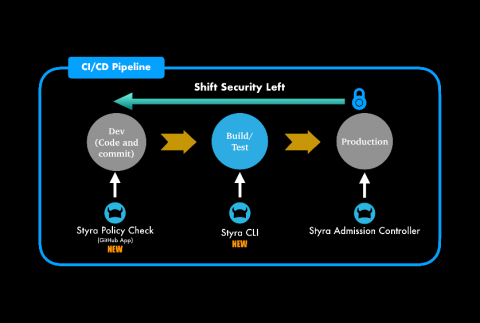
Enhancing Kubernetes Security by Shifting Security Left
In the rapidly evolving world of Kubernetes security & compliance, DevOps and DevSecOps teams are detecting security challenges and compliance issues later in the development & deployment cycles. We are excited to share new features and updates that help DevOps and DevSecOps teams detect issues and ensure compliance throughout the development cycle.
Centralized vs. Distributed Authorization: The CAP Theorem
One of the best parts of working on the Open Policy Agent at Styra is that we get to help people design authorization systems for both their platform and their custom applications. The other day we were talking someone through the design tradeoffs of authorization for their application, and the first decision they had to make was whether they wanted a centralized authorization system or a distributed authorization system. Both OPA and Styra support either, so we have no real bias.
What Is DevOps Maturity, and How Does It Relate to DevOps Security?
By now, many organizations have turned to DevOps as part of their ongoing digital transformations. This process has not been the same for any two companies. Indeed, organizations have embraced DevOps at their own place, and they’ve invested varying levels of time and budget into their nascent deployments.