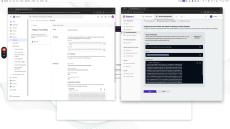
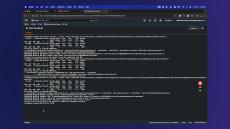
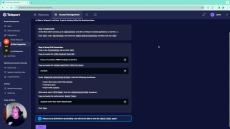
Teleport Database AWS Database Auto-Discovery
https://goteleport.com/docs/database-access/guides/aws-discovery/
- April 2024 (1)
- March 2024 (2)
- February 2024 (13)
- January 2024 (1)
- December 2023 (4)
- November 2023 (2)
- October 2023 (1)
- September 2023 (5)
- August 2023 (10)
- July 2023 (3)
- June 2023 (7)
- May 2023 (10)
- April 2023 (3)
- March 2023 (12)
- February 2023 (5)
- January 2023 (2)
- December 2022 (3)
- November 2022 (9)
- October 2022 (6)
- September 2022 (9)
- August 2022 (7)
- July 2022 (16)
- June 2022 (11)
- May 2022 (26)
- April 2022 (24)
- March 2022 (12)
- February 2022 (15)
- January 2022 (21)
- December 2021 (19)
- November 2021 (9)
- October 2021 (12)
- September 2021 (12)
- August 2021 (18)
- July 2021 (6)
- June 2021 (10)
- May 2021 (14)
- April 2021 (11)
- March 2021 (12)
- February 2021 (7)
- January 2021 (7)
- December 2020 (5)
- November 2020 (7)
- October 2020 (4)
- September 2020 (8)
- August 2020 (8)
- July 2020 (9)
- June 2020 (3)
- May 2020 (5)
- April 2020 (6)
- March 2020 (6)
- February 2020 (5)
- January 2020 (4)
- November 2019 (2)
- October 2019 (3)
- September 2019 (4)
- August 2019 (3)
- July 2019 (1)
- June 2019 (1)
- March 2019 (2)
- September 2018 (1)
- July 2018 (2)
Security and Compliance for Cloud Applications and Infrastructure. Cloud-native application delivery with robust Day-2 operations across many clouds, in restricted, regulated and remote environments.
Get compliance and security best practices out-of-the-box and make it easy for engineers to access SSH and Kubernetes environments across many clouds, data centers and edge devices. Deploy and Run Kubernetes applications on your customers' clouds, on the edge, and even in air-gapped server rooms, without overloading your DevOps teams.
Our products are open-source and based on open standards:
- Teleport: Access Kubernetes and Linux infrastructure across clouds, datacenters and IoT devices while enforcing industry best-practices for security and compliance.
- Gravity: Deploy and run cloud-native applications in hundreds of locations where security and compliance matter, on your customers' clouds or on the edge.
- Teleconsole: Teleconsole is a free service to share your terminal session with people you trust. Your friends can join via a command line via SSH or via their browser over HTTPS. Use this to ask for help or to connect to your own devices sitting behind NAT.
Grow your business across many production environments without having to worry about the vendor lock-in.