Keeper 101 - How to Set Biometric Login in Keeper on iOS
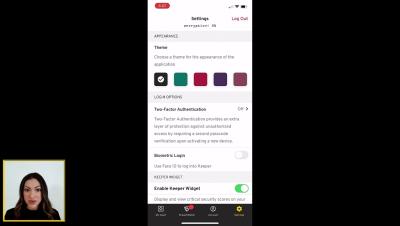
Biometric login, especially when paired with Keeper, is a time saving, convenient feature that allows you to login to Keeper with biometrics such as “Face ID”. To enable biometric login, navigate to the Settings screen in the Keeper app and toggle “Biometric Login”, “on”. Next time you want to log in to Keeper, simply tap the Face ID icon to initiate face recognition. Please note, Face ID must be configured in your device's settings before using it to login to Keeper.