Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SBOM
Create SBOM on Gradle with the CycloneDX Plugin
What is a Software Bill of Materials (SBOM)?
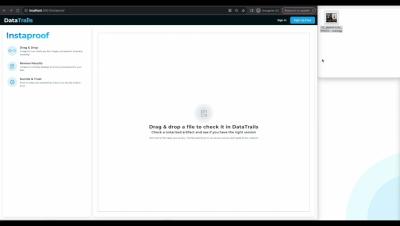
Safeguard the authenticity of your Dropbox files with DataTrails
Breakthrough fraud detection & content protection with watermarks + immutable audit trails
Combat the Erosion of Trust in Digital Media w/ Jon Geater CPO/CTO at DataTrails
EBOM vs. MBOM vs. SBOM: Key Differences & Best Practices
Managing all aspects of the product development cycle is a crucial element of a profitable company. Most businesses understand that an efficient product lifecycle depends on the proper positioning and management of the Bills of Materials (BOM), be it for product designing and manufacturing or software development. Getting all the BOMs right is the essential first step toward achieving operational efficiency.
Introducing SBOM support in Polaris | Synopsys
Bringing Immutable Audit Trails to Dropbox
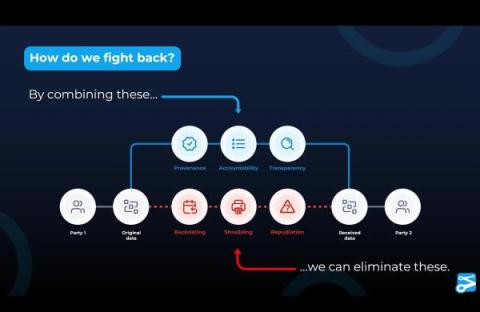
In the age of Gen AI, it is now apparent that we can no longer trust what we see and read. The fakers have the upper hand: while typical security approaches rely on scaling up teams, attacks scale at the press of a button. To safely move forward and realize the benefits Gen AI enables, we need a better trust model that adds integrity, transparency and trust to all data and a common provenance format that captures origin, authenticity and lineage information. We must verify data before we use it.
Detect Fakes and Prevent Misuse: Digital Content Integrity, Authenticity & Transparency
As supply chains continue to evolve and new Al technology becomes part of every business, traditional trust systems that rely on human interactions to verify and validate data will struggle to keep pace. Digital supply chain practices from media through software to physical goods must adapt to this changing global technology landscape. The innovations unleashed in GenAI have made it apparent that we can no longer trust what we see and read; we must verify data before we use it.