SBOM Explained: How SBOMs Improve Cloud-native Application Security
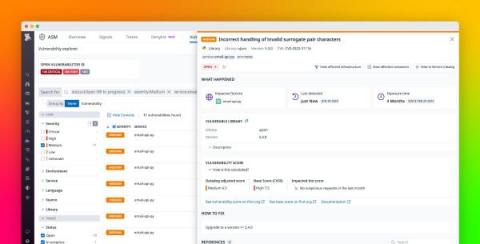
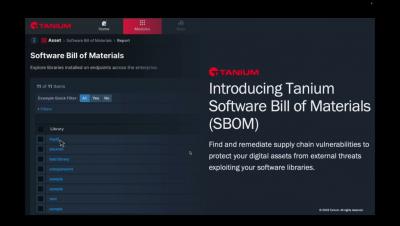
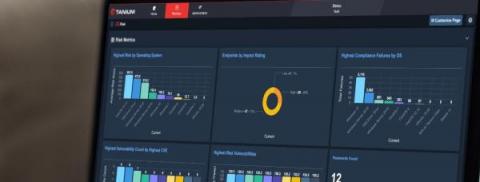
A staggering 96% of organizations utilize open-source libraries, yet fewer than 50% actively manage the security vulnerabilities within these libraries. Vulnerabilities are welcome mats for breaches from bad actors, and once they've entered your system, the impact can be colossal. A software bill of materials (SBOM) is an important tool for managing the security of open-source software.