How to Detect and Mitigate the 3CXDesktopApp Supply Chain Attack
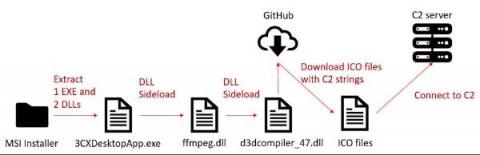
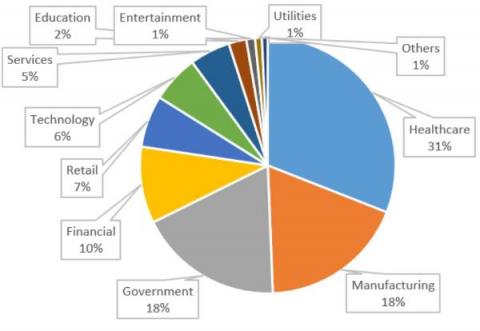
On March 29, researchers from two security companies identified an active campaign originating from a modified version of a legitimate, signed application: 3CXDesktopApp, a popular voice and video conferencing software. 3CXDesktopApp is developed by 3CX, a business communications software company. According to its website, 3CX has 600,000 client organizations and 12 million daily users.