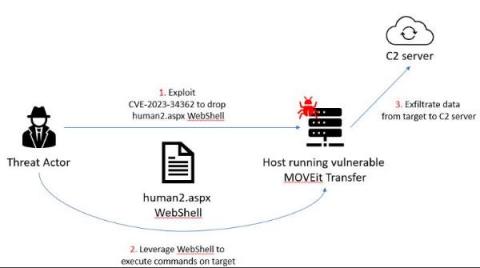
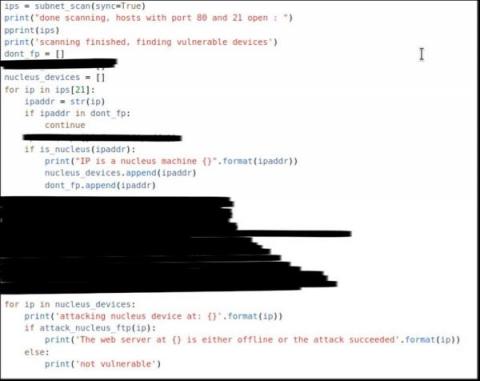
The 5 Riskiest Connected Devices in 2023: IT, IoT, OT, IoMT
Since 2020, Forescout Research – Vedere Labs has been tracking the riskiest devices on organizations’ networks. In 2020, we released the first Enterprise of Things Security Report, followed in 2022 with the Riskiest Connected Devices in Enterprise Networks report. Our reports are entirely based on data coming directly from connected devices.