Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Analytics
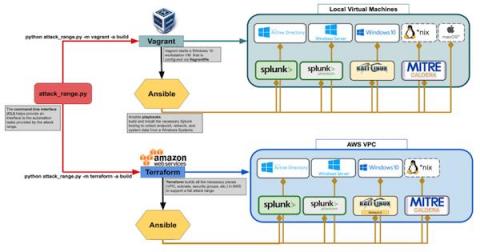
Splunk Attack Range Now With Caldera and Kali Linux
The Splunk Security Research Team has been working on new improvements and additions to the Splunk Attack Range, a tool that allows security researchers and analysts to quickly deploy environments locally and in the cloud in order to replicate attacks based on attack simulation engines. This deployment attempts to replicate environments at scale, including Windows, workstation/server, domain controller, Kali Linux, Splunk server and Splunk Phantom server.
COVID-19 Guide for Security Professionals
Devo Query Lookups
Redscan reveals Google security search trends during COVID-19 pandemic
At Redscan, we’ve set about shining light on some of these challenges by analysing how the crisis has affected online search behaviour in relation to cyber security and technology. The findings provide insight into how well-prepared businesses were for such an incident, the tools organisations are turning to support operations, and potential threats they are facing.
Recapping the Splunk for CMMC Solution Launch
On Wednesday, March 25th, we launched our Splunk for CMMC Solution with a webinar presentation to a diverse set of defense industrial base (DIB) participants and partners. As I discussed during the launch event, the Splunk for CMMC Solution provides significant out-of-the-box capabilities to accelerate organizations’ journeys to meet, monitor, track, and mature the cybersecurity practices required by the Cybersecurity Maturity Model Certification (CMMC).
4 Questions to Ask in Building a Security Operations Center
Building an in-house SOC represents a significant commitment, both financially and strategically, to securing your enterprise. In a report from the Ponemon Institute—based on a survey sponsored by Devo of more than 500 IT and security practitioners—67 percent of respondents said their SOC was “very important” or “essential” to their organization’s overall cybersecurity strategy.