Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Analytics
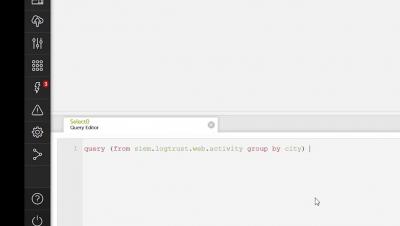
Activeboards [8] - Activeboards Calendars
What To Know About User Behavior Analysis
Devo Demisto Demo
Using Big Data In Auditing And Analytics
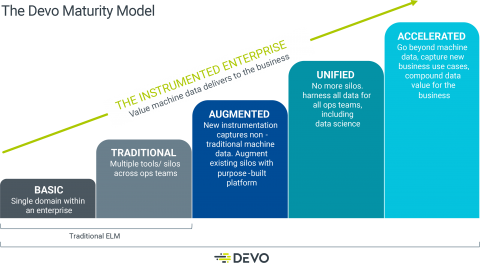
From Basic to Accelerated: The Devo Maturity Model
IDC says to estimate reaching 175 zettabytes of data by 2025, a 61 percent increase from today’s data volumes. Business leaders and IT executives overwhelmingly agree that they can do more to harness this data, but are we as an industry lacking for imagination? Or do we simply not know where to start or how to progress? To add insult to injury, today’s enterprises are stuck in the land of silos and replication, and too much data wrangling that consumes an already oversubscribed budget.
When Metrics and Logs are Unified, Good Business Ensues
If you’re reading this, you likely know what a log is, and what a metric is. But sometimes there are questions on their differences, whether you really need both, and if you should use dedicated solutions to manage each type. The answers? Yes, you need both; yes, they should be unified. Logs and metrics, aka machine data, are complementary.
Post-incident review and the big data problem
Across the board, security teams of every industry, organization size, and maturity level share at least one goal: they need to manage risk. Managing risk is not the same as solving the problem of cybersecurity once and for all, because there is simply no way to solve the problem once and for all. Attackers are constantly adapting, developing new and advanced attacks, and discovering new vulnerabilities.
What is Cybersecurity Analytics?
Security analytics is not a particular tool, rather it is an approach to cybersecurity. Thorough analysis of data in order to implement proactive security measures is the essence of security analytics. It includes gathering data from every possible source to identify patterns. Nobody can predict the future but with cybersecurity analytics, you can make pretty accurate, informed guesses about it.
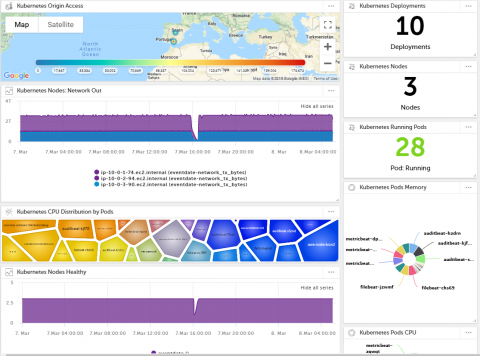
Introducing Devo Activeboards: A New Way to Visualize Machine Data
The data visualization space is crowded. There are lots of tools, each purporting to be the tool that solves your data woes and leads you to insight via illustrations. But while you may get good-looking graphs, you are probably not seeing the behind-the-scenes pain from IT: analytics dashboards and vertical applications take multiple meetings for gathering requirements, and they discover the direction wasn’t quite right the first time around.