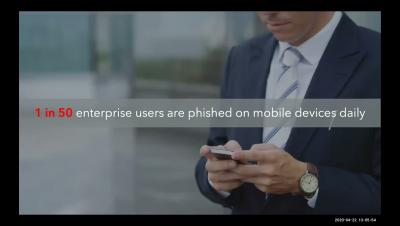
Email Security Trends Coming in 2022
Organizations are under constant threat of cybercrime. While there are many available attack vectors, email is the most obvious path towards a full network compromise. The notion that email security should be prioritized is emphasized during this time where more and more businesses are still working in a remote or hybrid dynamic environment.