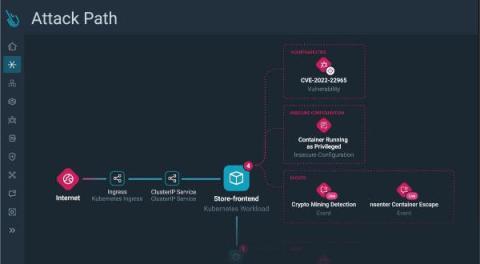
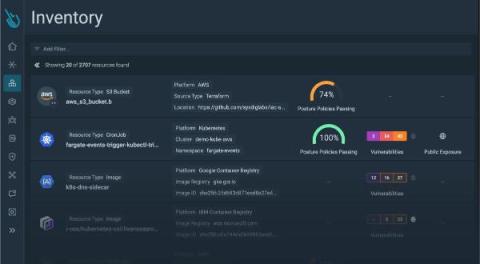
Unveiling Sysdig Secure Risks and Attack Path Analysis: Visualizing and Prioritizing Cloud Security Risks
While the cloud serves as a powerful accelerator for businesses, it also speeds up threat actors. Automation and an ever-increasing level of sophistication allow threat actors to execute complex attack chains in merely minutes, sometimes even less.The risk factors are amplified by the ability to chain together exploits and quickly move laterally in cloud environments, where a single breach could lead to a business critical compromise.