Exciting new features of Coralogix STA
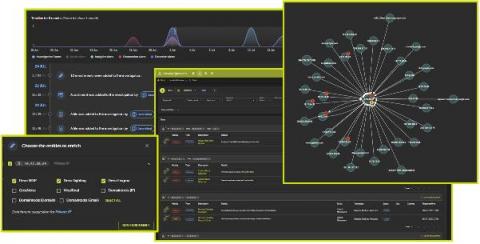
We at Coralogix, believe that cloud security is not a “nice-to-have” feature – something that only large organizations can benefit from or are entitled to have. We believe it’s a basic need that should be solved for organizations of any shape and size. This is why we built the Coralogix Security Traffic Analyzer (STA) tool for packet sniffing and automated analysis. Today we’re announcing several new features to our security product you’ll find interesting.