Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SecOps
Critical Remote Code Execution & Authentication Bypass Vulnerabilities in Aruba EdgeConnect Enterprise Orchestrator
Five tips for managing the cost of your security operations
With the global economy experiencing a slowdown, security teams are feeling the pressure to reduce costs without sacrificing security. But while it's important to be fiscally responsible, making cuts in the wrong areas can put your organization at risk. Malicious actors know that businesses are under even more pressure during times of economic turmoil.
Calculate the Cost of A Data Breach
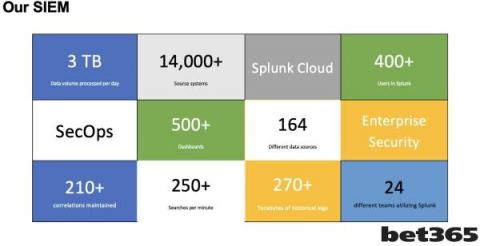
Inside the SecOps Team at bet365: Moving your SIEM to the Cloud
Hello, I love to look behind the scenes of SecOps teams to learn how they operate. Recently I had the pleasure to work with John Eccleshare, Head of Compliance and Information Security, at bet365 as John took the stage at Gartner Security and Risk Summit in London.
Security Basics: Incident Response and Automation
Incident response is one of the most challenging tasks that IT teams face. It's challenging not just because it typically involves many stakeholders and moving pieces, but also because teams usually face pressure to respond as quickly as possible. That's why investing in incident response automation is a wise choice. Although it may not be possible to automate every aspect of every incident response workflow, being able to automate at least the major elements of incident response will yield incident management processes that are faster, more reliable, and more consistent.Keep reading to learn about the components of incident response and which incident response activities to start automating.