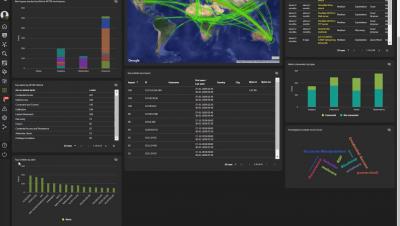
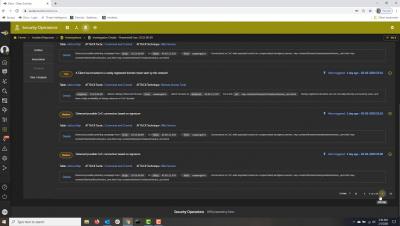
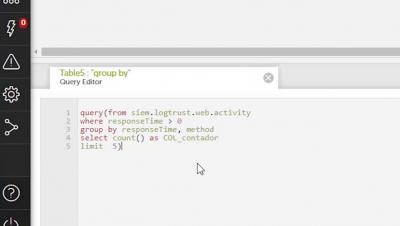
Devo Security Operations - Alert Triage
Security Operations improves SOC operations, from identification to response, by allowing analysts to gain complete visibility, reduce the noise, and focus on the threats that matter most. Instead of simply prioritizing alerts, Security Operations prioritizes what the analysts should investigate.