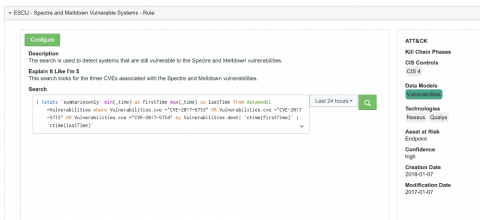
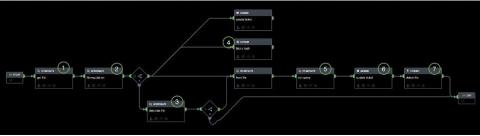
How to Conduct a Vulnerability Assessment
A considerable portion of cyber-attacks target simple and unnoticed security vulnerabilities, that is why conducting a thorough vulnerability assessment is vital for each and every organization. Read our article to learn more. As the technology advances, a vast majority of the business processes are realized online. Each and every day we share important files, send e-mails, conduct communication with our team and customers, and we do all these tasks online.