Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Unleashing the Power of Technology: How AI is the Next Big Leap! || Razorthorn Security
How Does IoT Contribute to Real-Time Grid Monitoring for Enhanced Stability and Fault Detection?
More decision-makers are investing in grid modernization efforts, knowing that doing so is necessary for keeping pace with modern demands. For example, smart grid fault-detection sensors could warn utility company providers of problems in real time, preventing costly and inconvenient outages. Technologies like the Internet of Things (IoT) can also improve stability. An IoT grid-monitoring approach allows authorized parties to oversee electrical infrastructure from anywhere.
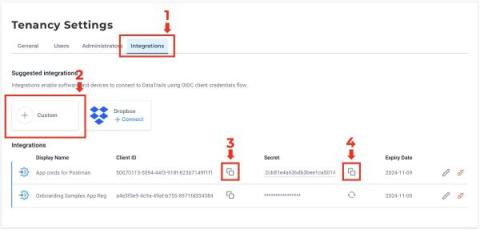
Postman Configuration for DataTrails
One of my favourite tools for playing with REST APIs is, of course, Postman. It can make interacting with DataTrails super quick and easy, and help you develop custom workflows for storing and validating your digital provenance and audit trails. Here’s a step-by-step guide to getting a robust Postman set-up configured, and if you head over the Postman public collections you’ll find a link to a pre-baked DataTrails Postman collection with this done for you, along with some example requests.
Cloud Watching Report: Key Takeaways
The capabilities of cloud computing have changed the digital landscape significantly, and the popularity of cloud solutions only continues to increase. According to Gartner, the market for public cloud services is expected to surpass 700 billion USD by the end of 2024. The growth of cloud technologies presents a wealth of new opportunities for IT teams but also brings a host of security challenges.
Coralogix Receives AWS MSSP Competency
With the increasing sophistication and frequency of cyber threats, companies often rely on partners to help provide security services and solutions. Amazon Web Services (AWS) Managed Security Service Provider competency is a hallmark of reliability for MSSPs and other vendors, signifying their capability to provide effective security solutions on AWS’s robust platform.
Demystifying the AWS shared security responsibility model
Most cloud providers use a shared security responsibility model, meaning they secure some areas of the environment but expect the customer to establish security controls in others. AWS is one of the many cloud providers that follow the concept of shared responsibility. Generally speaking, they split responsibility into two categories. AWS focuses on the security of the cloud, such as the infrastructure that runs all AWS services.
Securing the Generative AI Boom: How CoreWeave Uses CrowdStrike to Secure Its High-Performance Cloud
CoreWeave is a specialized GPU cloud provider powering the AI revolution. It delivers the fastest and most consistent solutions for use cases that depend on GPU-accelerated workloads, including VFX, pixel streaming and generative AI. CrowdStrike supports CoreWeave with a unified, AI-native cybersecurity platform, protecting CoreWeave’s architecture by stopping breaches.
Securing Your Web Applications and APIs with Dynamic Analysis
Web applications are one of the most common vector for breaches, accounting for over 40% of breaches according to Verizon's 2022 Data Breach Report. Ensuring that your web applications are sufficiently protected and continue to be monitored once they are in production is vital to the security of your customers and your organization.