Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Teleport
Best Practices for Secure Infrastructure Access
Technologies build on other technologies to compound growth. It’s no coincidence that of the companies with the highest market capitalization within the US, the first non-tech company is the eighth one down: Berkshire Hathaway. Nor is it a coincidence that tech startups can take their valuation into the 10 digits in a flash on the backs of other tech companies. This pace of growth can only be afforded by the innovation of new technology.
Celebrate Open Source Day with Gravitons on September 4th!
I was going through a row of photography books in an antique store when I got a call from Bucky Moore, our lead investor and a board member. “Let me know if you need anything from me. This is getting serious,” he said. He seemed concerned. It was Sunday, March 22nd, right after the shelter in place order went in effect here in California. The next day, COVID-19 was no longer just in the news, it was everywhere.
Webinar | How Decisiv Scaled Global Remote SSH Access and Remained Compliant With Teleport
How To Use Teleport - Using Slack With Approval Workflow
How I Found Myself in a Command Line vs. GUI Meeting
“Ev, do you have time later today to discuss the new web GUI for the command line terminal?” said the Slack message. It came from Alex, our user experience chief and the product in question is the SSH client. Part of me was worried. The command line environment had a sanctuary where I found peace and happiness away from the world of browser-based tools.
Webinar | Best Practices for SSH + Auditing w/ Panther | Gravitational | Gus Luxton | Jack Naglieri
SSH vs. kubectl exec
Let’s have a look at two popular ways of opening remote shells: the good ol’ ssh and its modern counterpart, kubectl exec. Below, I will only look at the “kubectl exec” subcommand and its friends. kubectl itself is a swiss-army knife for all things Kubernetes. Comparing all of it to ssh is like comparing systemd to BSD init. Also, I will use “SSH” to mean “OpenSSH”, which is the de-facto standard for SSH protocol implementation.
How To Use Teleport: Using GitHub for Single Sign On (SSO)
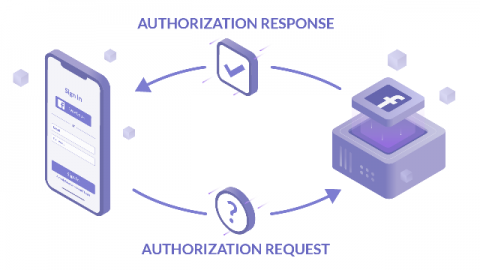
How OIDC Authentication Works
Did you know that in the United States, the Social Security Number was never intended to become the defacto method for physical identification? On its surface, this may come as a shock given how ubiquitously SSNs are used for this exact reason, but looking beneath the surface, we find that SSNs are terrible forms of identification. Ignoring the security concerns of a nine digit numeric code, an SSN is not for universal identification.