Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Datadog
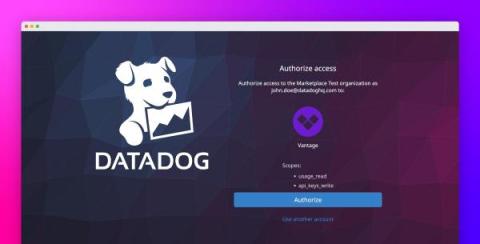
Authorize your Datadog integrations with OAuth
OAuth is an authorization protocol that allows apps to securely request user data without requiring the user to enter their sensitive credentials (e.g., API keys, application keys, etc.). Datadog API-based data integrations now fully support OAuth.
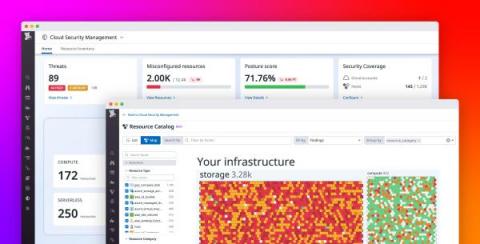
Add security context to observability data with Datadog Cloud Security Management
Organizations are rapidly migrating their infrastructure to the cloud, enabling them to modernize their applications and deliver more value to their customers. But this transition creates significant security risks that they may be unable to keep pace with. For example, cyber attacks on cloud resources are becoming more sophisticated and prevalent. Additionally, organizations often rely on legacy, disjointed security tools that don’t integrate well with cloud-native infrastructure.
The State of AWS Security
In the cloud, securing identities and workloads is both paramount and complex. Inventories of AWS customer security breaches help us learn from publicly disclosed incidents—but until now, not much concrete data has been shared around the usage of security mechanisms that could have helped prevent these incidents. For this report, we examined real-world data from a sample of more than 600 organizations and thousands of AWS accounts that use the Datadog Cloud Security Platform.
Best practices for securely configuring Amazon VPC
Amazon Virtual Private Cloud (Amazon VPC) is an AWS service that enables you to launch AWS resources within your own virtual network. Because you can deploy VPCs in separate regions and other VPC components themselves are deployable across different Availability Zones, VPC-hosted environments tend to be highly available and more secure.
Monitor flow logs to ensure VPC security with Datadog
In part 1 of this series, we looked at the common components of an Amazon VPC including CIDR blocks, subnets, firewalls, and route tables. We also looked at approaches for how to configure those components securely.
Datadog on Web Security Standards
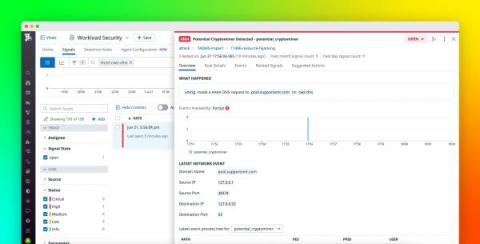
Identify security vulnerabilities with DNS-based threat detection
The Domain Name System (DNS) is responsible for mapping client-facing domain names to their corresponding IP addresses, making it a fundamental element of the internet. DNS-level events provide valuable information about network traffic that can be used to identify malicious activity. For instance, monitoring DNS lookups can help you see whether a host on your network attempted to connect to a site known to contain malware.
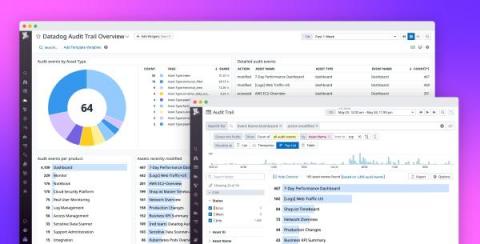
Ensure compliance, governance, and transparency across your teams with Datadog Audit Trail
In order to maintain compliance, enforce governance, and build transparency, teams across your organization need deep insight into how their users and automation interact with Datadog. For stakeholders in leadership roles, such as CIOs and CDOs, knowing what actions users took and when is essential for spotting gaps in enablement, budgeting, and reporting, as well as building a modern compliance strategy for the organization as a whole.
The Confluence RCE vulnerability (CVE-2022-26134): Overview, detection, and remediation
On May 31, 2022, a critical vulnerability in Atlassian Confluence Server and Confluence Data Center was disclosed by Volexity. While conducting an incident response investigation involving internet-facing servers with the Confluence server installed, Volexity determined that the servers were compromised and attackers were launching successful remote code execution (RCE) exploits.